Andreja is usually a articles expert with around half ten years of expertise in putting pen to digital paper. Fueled by a enthusiasm for cutting-edge IT, he uncovered a house at phoenixNAP where he gets to dissect intricate tech matters and crack them down into simple, quick-to-digest content.
people and devices are destined to live in an ever-closer romance. To make it a cheerful relationship, we have to better address the moral and authorized implications that data science have.
This allows providers securely regulate a escalating volume of e-mail attachments, detachable drives and file transfers.
though the risk profile for data in transit and data in use is higher than when it’s at relaxation, attackers frequently concentrate on facts in all three states. As opportunists, they may try to look for any property or mental house that happen to be straightforward to breach.
just before deploying encryption at rest (or another variety of safety method), you must to start with map your most sensitive enterprise and consumer data. Data classification varies concerning firms, but an outstanding place to begin is to determine:
employing computerized protocols can even make certain that correct defense steps are activated when data shifts amongst states, making sure that it usually has the very best level of security.
When working On this new mode, the CPU is during the safe earth and might obtain all of the product’s peripherals and memory. When not functioning In this particular method, the CPU is within the Non-protected World and just a subset of peripherals and particular ranges of physical memory can be accessed.
to illustrate you wish to send out a private information in your Good friend. You'd use AES to encrypt your message having a secret crucial that only both you and your Good friend know. Here's a Python case in point utilizing the pycryptodome library:
Data is in use when it’s accessed or consumed by an employee or company application. no matter whether it’s getting browse, processed or modified, data is at its most susceptible in this state because it’s directly available to an individual, which makes it susceptible to assault or human error – equally of which often can have substantial consequences.
lots of the programs we use daily, like electronic mail or collaboration tools, are hosted in the cloud. Encryption for these applications requires securing the data that travels among your system plus the cloud server. This stops hackers from intercepting read more sensitive data even though It is really in transit.
Blockchain technology even more boosts this security framework by supplying a decentralized ledger that assures data integrity and transparency, making it just about extremely hard for unauthorized events to alter facts.
This encryption system works by using two keys, the public critical to encrypt as well as non-public essential to decrypt. this technique enhances protection by eradicating solution keys that must be shared nevertheless it really is slower.
And there are various much more implementations. Though we can implement a TEE in any case we would like, an organization called GlobalPlatform is driving the standards for TEE interfaces and implementation.
When you see https:// In the beginning of a website deal with, this means their link employs SSL or TLS. This allows secure your passwords and all your information and facts while they are now being transferred to the web site.
 Spencer Elden Then & Now!
Spencer Elden Then & Now! Tony Danza Then & Now!
Tony Danza Then & Now! Daniel Stern Then & Now!
Daniel Stern Then & Now!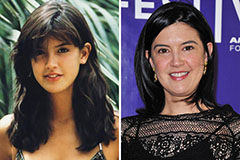 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Traci Lords Then & Now!
Traci Lords Then & Now!